Managing Resource Scarcity in Enterprise Information Security ? Part 2
In our last post (Resource Scarcity in Information Security ? Part 1) we discussed the options for how to deal with resource scarcity and why the only effective strategy involves reducing the team?s scope. In this post I will dive into how we can reduce the information security team?s scope of work while preserving the value delivered to the business to the greatest extent possible.
So, how does ?doing less? actually work? While there are many models for this, below is a simple 5-step model which can work as a template for your team.
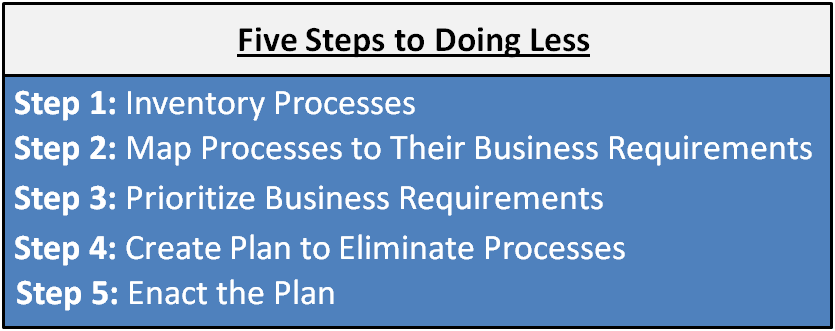
With Step 1, you need to ensure you have a solid understanding of what your department does. I?ve found that many infosec teams don?t have a great understanding of all the processes they perform, and more importantly, don?t understand how those processes map back to the needs of the business. So start by creating a list of all processes you are performing. For each of those processes, determine exactly what business requirements they are meeting. Are there regulatory requirements for this task? Are you meeting the contractual needs of clients? Or maybe you will find that you?re just doing this because it?s always been done.
In Step 2 you start prioritizing. You?re not prioritizing the security process; you are prioritizing the BUSINESS REQUIREMENT. This step requires intimate communication with the business itself. You need to understand how your service offerings add value. Involve operations, IT, marketing, HR, legal and compliance to figure out what they get from you, and what they need to continue to get.
The prioritization process has two positive side effects. In addition to helping you determine the business priorities, it provides the information security team with a better understanding of exactly how it enables the business. This helps security staff become more engaged and better aligned to the business overall. Additionally, this process helps the business become aware of the impacts of resource limitations. This process will prepare them for later steps, when some security offerings are changed.
Step 3: Identify those processes you want to stop supporting. The eliminated process should be identified by a combination of the business needs it addresses, the resources required to support it, budgetary cycles, and other business realities. While the security leadership may be the ones to gather this information and make recommendations, it?s important to share the findings with other business leaders and stakeholders. Let a diverse group contribute here to gain their input. A collaborative approach to deciding what processes to drop will not only provide multiple perspectives (helping reduce the possibility that a critical process is cut), but it will help get these stakeholders on the bus, to support the rocky moments that may result in eliminating a process.
In Step 4, create de-implementation plan for the process. Critical to this step is determining how you will meet whatever business needs the process was previously addressing. Do you have another method to meet those needs? Perhaps the task can be handled by another department, another system, or by a more efficient manual process. Or very possibly, due the shrinking resources, that service is going to be discontinued. Regardless, this needs to be widely communicated and understood by all stakeholders, so they understand in advance how their environment is changing. The plan should identify all personnel and technical resources to eliminate the process, along with a communication plan and a test plan to ensure that the process was a success. This is the place for ensuring that you have detailed technical procedures on how to extricate this system.
Step 5: Here you enact the plan developed in Step 4. The quality of your plan is likely to dictate success here. The better you document and test in advance, the more smoothly this will go. Were you thorough in your research in identifying all the stakeholders in Step 2? Were your technical plans solid in Step 4? Planning ahead is the key to an easy implementation.
While nobody likes hearing that budgets are cut, or headcount is reduced, every change is also an opportunity. It?s an opportunity to redefine your security department, and reevaluate whether you?re getting value from every tool and process that?s a part of your arsenal. By proactively choosing where you stop focusing, and understanding exactly what the business impacts of that will be, you may even find that you will walk away from this exercise with a better understanding of the business, your security offerings, and with an overall improved security position.
Connect with Robb on Google+
Colorado shootings dark knight rises Aurora shooting James Eagan Holmes jeremy lin Sage Stallone Mermaid Body Found
No comments:
Post a Comment